
Data security is vital. In fact, the security, confidentiality, and availability of your sensitive data are all essential. Given that in 2022 over 60 percent of all corporate data is stored in the cloud and cyberattacks and data breaches are on the rise, concern about how secure your data actually is has increased. Further complexity is added as data protection requirements for the cloud are constantly evolving.
There are a number of security frameworks available that protect the security, confidentiality, and availability of data. But ensuring your data stays secure can go a step further. Let’s see why we chose the ISO 27001 certification to ensure the best security measures for your data.
What is the difference between ISO 27001 and SOC 2?
ISO 27001 and SOC 2 share the same focus. Both conduct an external audit that measures against security controls, including processes, policies, and technologies designed to protect sensitive information. It is their approach that is different.
The main difference is that SOC 2 is primarily focused on proving you’ve implemented security controls that protect customer data, while ISO 27001 also asks you to prove you have an operational Information Security Management System (ISMS) in place to manage your InfoSec program on a continual basis.
What is SOC 2 compliance?
SOC 2 is a framework applicable to all technology services companies that store customer data in the cloud. The framework ensures that organizational controls and practices effectively safeguard the privacy and security of customer and client data.
The audit for SOC 2 is performed by an independent Certified Public Accountant (CPA) or accountancy organization. The outline of the resulting reports is defined by the American Institute of Certified Public Accountants (AICPA) and, as such, is usually applicable to U.S. companies.
The report is not a prescriptive list of controls, tools, or processes. Rather, it cites 64 criteria required to maintain robust information security. These criteria can be broken into the five trust service principles of: security, availability, processing integrity, confidentiality, and privacy of customer data as a framework for safeguarding data. Companies are allowed to select and adopt the practices and processes relevant to their own objectives and operations.
What is ISO 27001 compliance?
ISO 27001 is an international standard for protection requirements and controls for information and systems. As a standard, it’s made up of various requirements set out by ISO (the International Organization for Standardization) – an impartial group of international experts. ISO has verification bodies worldwide that provide a formal security certification to successful applicants. It is considered one of the highest international security standards.
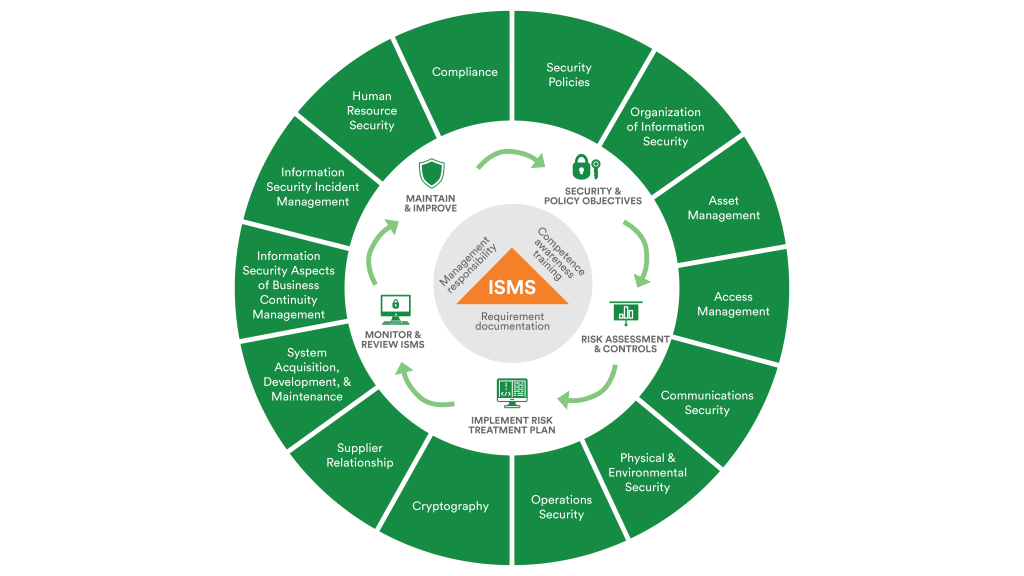
To be certified with ISO 27001 an Information Security Management System (ISMS) needs to be implemented. There are seven clauses for establishing, implementing, and maintaining an organization’s ISMS. The focus of these are: securing information, reducing the risk of cyber attacks, helping understand threat landscapes, and protecting confidentiality via policies, procedures, and technical controls.
These seven comprehensive requirements have 114 suggested controls spanning encryption, firewalls, infosec policies, physical access controls, and much more.
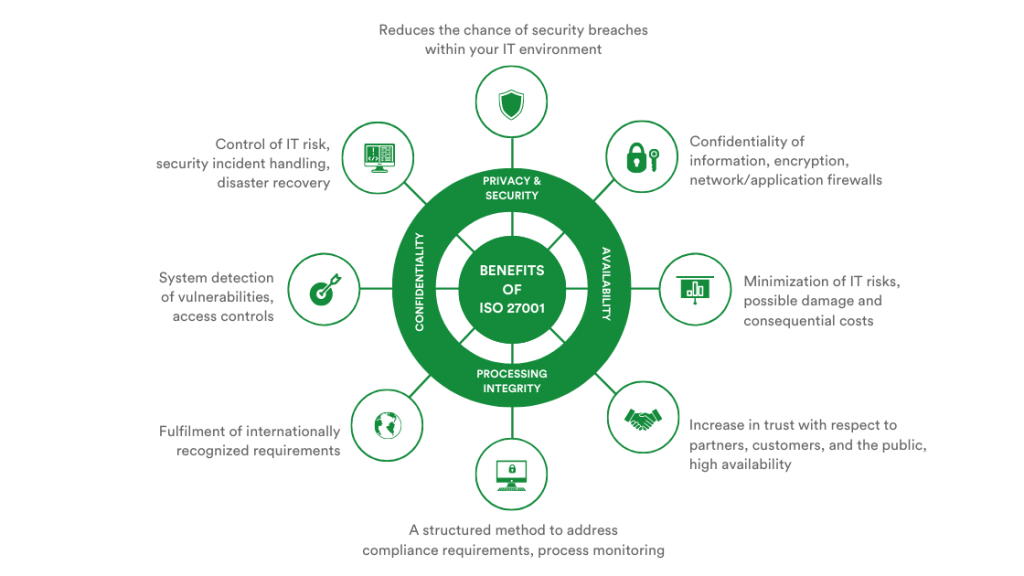
What are the benefits of obtaining a data security standard?
By establishing and maintaining a documented system of controls and management, risks can be identified and reduced. SOC 2 and ISO 27001 overlap in their standards, but it is the rigidity of the process and regulatory body that differentiates them.
Benefits of SOC 2
Being SOC 2 compliant assures your customers and clients that you have the infrastructure, tools, and processes to protect their information from unauthorized access both from within and outside the firm. It supplies you with a report that can be shared with customers.
Benefits of ISO 27001
In addition to the benefits of infrastructure, tools, and processes to protect information from unauthorized access, achieving ISO 27001 certification shows that a business has put the framework in place to protect client and employee information from getting into unauthorized hands, and ensures that information is accurate and can only be modified by authorized users. By establishing a framework, security measures are monitored, maintained, and approved. If a business meets an ISO standard, it will receive both a report and certification. The rigorous process of being ISO 27001 certified also means that you have achieved compliance with the European Union General Data Protection Regulation (EU GDPR) regulations.
Deciding factors when choosing between SOC 2 and ISO 27001 for data security
Both SOC 2 and ISO 27001 help organizations demonstrate control strength and effectiveness in maintaining data security. Organizations should review their needs and critical factors for their industry, region, customers, and partners to help determine which standard is most fitting. Here are some questions to consider when determining which is the right one for your organization.
Where are your customers located?
If your customers are all in the United States, SOC 2 will be more familiar with your client base. If your customers are US-based as well as having international offices, they will recognize ISO 27001. ISO 27001 has gained popularity worldwide due to the strict privacy requirements of GDPR and CCPA.
What data security focus is most important to your customers?
SOC 2 focuses on security controls implemented to protect customer data, whereas ISO 27001 has a more operational view of the scope of controls required to protect an organization and all its sensitive data continuously.
How do you need to prove compliance?
A SOC 2 audit supplies an attestation report whilst ISO 27001 provides audit reports and an ISO certificate if businesses pass. Given that SOC 2 checks for the existence of security controls, annual audits are required to maintain compliance. With ISO 27001 requiring the implementation of an ISMS, which ensures that an organization maintains security standards, recertification is every 3 years with external audit checks annually.
Why PageProof chose ISO 27001 for its data security
We are extremely proud to be the only fully-encrypted online proofing platform – wrapping your data in a triple layer of protection. In fact, we hold patents for our unique encryption sharing engine in numerous regions around the world – the United States, European Union, New Zealand, and Australia.
But we wanted to take our data security one step further. PageProof customers are located worldwide and operate in a range of industries. Hence, we chose the most robust framework for our data security standard. PageProof’s ISMS has been certified to ISO 27001:2013.
Meaning you can rest assured that not only your data in relation to your proofs, but also all of your sensitive customer-related data is kept secure at all times. And, an operational ISMS is in place for ongoing security checks and measures.

Data security is of the utmost importance in a digital world. Two of the most popular frameworks to embed data security in organizations are SOC 2 and ISO 27001. It depends on your specific requirements which framework is more suitable for your business. PageProof chose ISO 27001 for our data security standard due to the robustness of the certification, meaning that our customers could feel confident with our data security wherever they are. And we are proud to have achieved ISO 27001 information security certification, which represents the recognition of our commitment to information security management by global standards.

1 Comment
Comments are closed.